1. Prerequisites:
1. User accounts must be hybrid user identities, which means you'll also need AD DS and either Microsoft Entra Connect or Microsoft Entra Connect cloud sync. You must create these accounts in Active Directory and sync them to Microsoft Entra ID.
2. Session hosts should be either Microsoft Entra joined or Microsoft Entra hybrid joined. In this case, they are Microsoft Entra hybrid joined.
3. A system joined to your domain is required to configure the permissions on the Azure Files share.
4. A Storage account and a File share need to be created. I have already covered the creation process in my other blog: Comprehensive Guide to Configuring Azure Storage Accounts with Premium File Share for Azure Virtual Desktop: Including Troubleshooting Tips - A T L
2. Enable Microsoft Entra Kerberos authentication on Azure Files:
1. Search for the storage account in the global search and select the one that was created.
2. Under 'File share settings,' next to 'Identity-based access,' you’ll see 'Not Configured.' Click on it.
3. Click 'Set up' under Microsoft Entra Kerberos.
4. Check the box for Microsoft Entra Kerberos.
5.Under 'Domain name' and 'GUID,' enter the respective details. You can find these details by running the 'Get-ADDomain' command on a domain-joined VM.
6. Click on Save.
3. Grant admin consent to the new service principal:
1. Open Microsoft Entra ID. In the service menu, under 'Manage', select 'App registrations'. Select 'All Applications'. Select the application with the name matching [Storage Account] <your-storage-account-name>.file.core.windows.net.
2. In the service menu, under Manage, select API permissions.
3. Select Grant admin consent for [Directory Name] to grant consent for the three requested API permissions (openid, profile, and User.Read) for all accounts in the directory.
4. Select Yes to confirm.
4. Disable multifactor authentication on the storage account:
1. If MFA is enabled in the environment using the Conditional Access policy, make sure to exclude the storage account from this policy.
5. Assign share-level permissions:
1. Check the step-by-step guide on how to assign RBAC roles to users and groups on the file share by clicking: Comprehensive Guide to Configuring Azure Storage Accounts with Premium File Share for Azure Virtual Desktop: Including Troubleshooting Tips - A T L
2. I have assigned the 'Storage File Data SMB Share Contributor' role to the AVD Security group created for accessing AVD. The 'Storage File Data SMB Share Elevated Contributor' role is assigned to the admin account, which can be used to assign NTFS permissions on this share.
6. Configure directory and file-level permissions:
1. Copy the UNC path "https://strdem0302.file.core.windows.net/profiles" from the File Share.
2. Change it to '\strdem0302.file.core.windows.net\profiles' and open it in File Explorer. Right-click and select 'Properties.'
3. Select the 'Security' tab and click Advanced.
4. Click Disable inheritance.
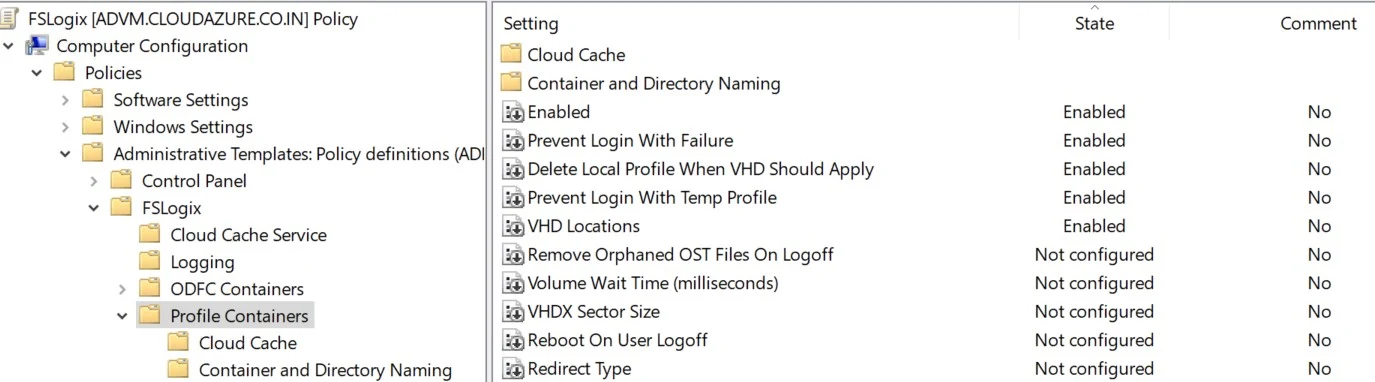
1. Configure the GPO Policy: Computer Configuration > Policies > Administrative Templates > FSLogix > Profile Containers
9. Testing:
1. These are the session hosts that were created.
2.Since these are Hybrid Entra ID-joined devices, they also appear in Entra ID.

3. Once the user logs into AVD, the profile is successfully created in the Azure file share.
4. You can also run the klist command to display Kerberos tickets.10. Key Findings:
1. Windows multi-session client operating systems don't support Intune Policy CSP (Configuration Service Provider)
4. Download the ADMX and ADML files for Kerberos and FSLogix GPO policy settings to make them appear in your Group Policy Management.

























Comments
Post a Comment