3. Data protection
Sensitivity labels are like digital "tags" or "stickers" that you apply to files, emails, or documents to indicate how sensitive or private they are. For example: You might label a document as "Confidential" if it contains sensitive information. A report could be labeled "Public" if it’s okay to share with everyone.
These labels help people and systems know how to handle the information – like whether it should be kept private, shared with certain people, or protected with special security measures. It's like putting a "Confidential" stamp on a paper document to tell people it should be handled carefully.
In addition to sensitivity labels, Data Loss Prevention (DLP) is another important tool to protect sensitive information. DLP helps make sure that private or sensitive data doesn't get shared or leaked by mistake. It’s like having a security guard who stops confidential information from leaving the company or being shared with the wrong people.
For example, DLP can:
Block an employee from accidentally sending a confidential document to the wrong email address.
Prevent sensitive data from being uploaded to public websites or shared insecurely.
Prerequisites:
1. Admin needs to have a Compliance administrator role.
2. You need to have the appropriate license to use this functionality. I am using a Microsoft 365 Business Premium license.
1. DP-1: Discover, classify, and label sensitive data
Features: Sensitive Data Discovery and Classification
1. Enable Audit logging before working with sensitivity labels, as some functions require it to be turned on. If you don't turn it on, you might encounter errors during the process.
Note: It may take up to an hour for the audit to be activated.
Go to https://purview.microsoft.com/
Click on Solutions-Audit.
Click on Start Recording user and admin activity
2. To apply sensitivity labels to Teams, SharePoint sites, and Microsoft 365 Groups, you must first complete the necessary steps to enable the feature. This is because, during the sensitivity label creation process, the "Groups and Sites" option will be greyed out. Therefore, it is advisable to complete this prerequisite beforehand.
- Open a PowerShell prompt on your computer and run the following command:
- Install-Module Microsoft.Graph -Scope CurrentUser
- It would take around 5-10 minutes for the modules to be downloaded and installed.
- Run the command: Install-Module Microsoft.Graph.Beta -Scope CurrentUser


- Run the command: Connect-MgGraph -Scopes "Directory.ReadWrite.All"
- Enter the credentials

- Run the command: Get-MgBetaDirectorySettingTemplate
- This cmdlet call returns all templates that are available

- To add a usage guideline URL, first you need to get the SettingsTemplate object that defines the usage guideline URL value; that is, the Group. Unified template
- Run the command:
- $TemplateId = (Get-MgBetaDirectorySettingTemplate | where { $_.DisplayName -eq "Group.Unified" }).Id
- $Template = Get-MgBetaDirectorySettingTemplate | where -Property Id -Value $TemplateId -EQ

- Create an object that contains values to be used for the directory setting. These values change the usage guideline value and enable sensitivity labels. Set these or any other setting in the template as required
- Run the command:
- $params = @{
- templateId = "$TemplateId"
- values = @(
- @{
- name = "UsageGuidelinesUrl"
- value = "https://guideline.example.com"
- }
- @{
- name = "EnableMIPLabels"
- value = "True"
- }
- )
- }

- Create the directory setting by running: New-MgBetaDirectorySetting -BodyParameter $params
- You can read the values by using the following commands:
- $Setting = Get-MgBetaDirectorySetting | where { $_.DisplayName -eq "Group.Unified"}
- $Setting.Values
- To remove the value of UsageGuideLinesUrl, edit the URL to be an empty string.
- Run the command:
- $params = @{
- Values = @(
- @{
- Name = "UsageGuidelinesUrl"
- Value = ""
- }
- )
- }

- Update the value by running: Update-MgBetaDirectorySetting -DirectorySettingId $Setting.Id -BodyParameter $params

- Apply the new settings by running:
- $params = @{
- Values = @(
- @{
- Name = "EnableMIPLabels"
- Value = "True"
- }
- )
- }
- Update-MgBetaDirectorySetting -DirectorySettingId $grpUnifiedSetting.Id -BodyParameter $params
- Verify that the new value is present by running: $Setting = Get-MgBetaDirectorySetting -DirectorySettingId $grpUnifiedSetting.Id
- $Setting.Values
3. Enable Co-authoring for files with sensitivity labels. This setting allows users in your organization to co-author in Office desktop documents that are encrypted by using sensitivity labels.
Go to Settings-Solution Settings-Information Protection. Check the box for Turn on co-authoring for files with sensitivity labels.
Click Apply.

4. Create and Publish Sensitivity Labels
5. Go to Solutions-Information Protection6. Click on Sensitivity labels. You may see a pop up that says Extend labelling beyond Microsoft 365. You may click Turn on.
7. Click Yes.
8. Click + Create a label.
9. Give an appropriate Name and Display Name.
10. For Label Priority, the default option is Highest. Let's keep it as is.
11. Give a suitable description for the users and the admins.
12. Select the appropriate color.
13. Click Next.

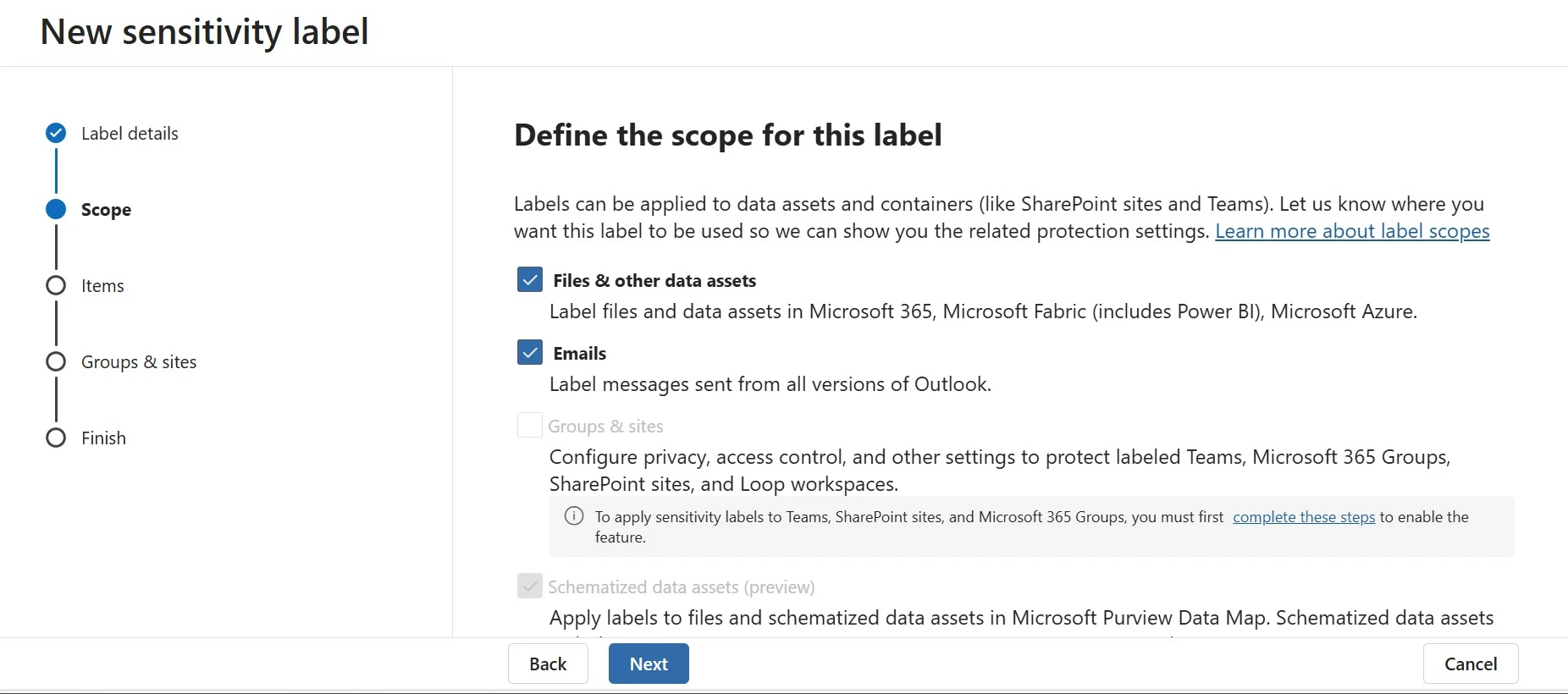
14. Check all four boxes. The third box, Groups & Sites, is not greyed out because we ran PowerShell commands during the prerequisites. The fourth box, Schematized Data Assets, is not greyed out because we enabled audit logging in the prerequisites.
15. Click Next.
16. Check both boxes—Control access and Apply content marking.
17. Click Next.
18. Check the box-Configure access control settings
19. For Assign Permissions now or let users decide? select Assign permissions now.
20. For User access to content expires select Never.
21. For Allow offline access select
Always.
22. Click on Assign permissions. Select +Add any authenticated users.
23. Click Next.
24. Enable Content marking. You can add a watermark, header and footer depending on the requirement.
25. Click Next.
26. You can enable Auto-labeling. However, it requires Azure AD Premium P2 license.
27. Click Next.
28. Check all the 3 boxes. Click Next. 29. I have selected Private. You can choose an option based on your requirements.
30. Click Next.
31. Select the appropriate options based on the requirements, then click Next
32. Select the appropriate options based on the requirements, then click Next
33. Click Create Label.
34. Select Don't create a policy yet and click on Done.
35. Click on Publish labels.
36. Click on choose sensitivity labels to publish.
37. Select the label we created and click on Add.
38. Click Next.
39. If you have an E5 license and wish to restrict the policy to a specific set of users or groups, please proceed. Otherwise, click Next
40. Select the required users and groups. Click Next.
41. Select all that apply. I have chosen the first two options. Click
Next.
42. Here, it asks whether you want to apply the label we created as the default or allow users to select a label based on the sensitivity of their documents. I am choosing None, letting users select the appropriate label
43. I have selected both boxes. You can choose based on your requirements. Click
Next.
44. Check the box as appropriate and click
Next. 
45. Check the box as appropriate and click Next.
47. Give a meaningful name to the policy. Click Next.

48. Click Submit.

Demo-Sensitivity Labels:
You can see that the user is given an option to label the document they are working on.
2. DP-2: Monitor anomalies and threats targeting sensitive data
Features: Data Leakage/Loss Prevention
1. Click on Solutions-Data Loss Prevention.
2. Click on Policies- +Create policy
3. You may select a template based on the following categories: Financial, Medical and Health, Privacy or Custom. For this demonstration, I am selecting the Custom template.
4. Click on Custom->Custom policy->Next.

5. You can either proceed with the default name and description or customize them to suit your specific requirements. Click Next.
6. If you have an E5 license and wish to restrict the policy to a specific set of users or groups, please proceed. Otherwise, click Next
7. Select all the applicable locations where you want this policy to be enforced. If you wish to restrict the policy to specific groups or users, click on
Edit and select only the required ones. Click Next.
 8. The box for 'Create or customize advanced DLP rules' will be checked by default. Click 'Next' to proceed.
8. The box for 'Create or customize advanced DLP rules' will be checked by default. Click 'Next' to proceed.
9. Click + Create rule.
10. Give a meaningful name and description.11. Click on +Add Condition.
12. Under Add condition click on Content contains
13. Give a meaningful group name.
14. Under Group operator select Any of these.
15. Click on Add-Sensitive Info types.
16. You may select the appropriate sensitive types based on the customer's region.
17. Click on Add.

18. Under Actions tab, click on + Add an action and then select-Restrict access or encrypt the content in Microsoft 365 locations.

19. I have selected the box-Block everyone.
20. Under User notifications I have turned it ON.
21. Rest all the settings I have kept the default as is.
22. Click Save.
23. Click Next.
24. Check the box-Turn the policy on immediately.
25. Click Next.

26. Click Submit.
27. Click Done.
3. DP-3: Encrypt sensitive data in transit
Features: Data in Transit Encryption
Transport Layer Security (TLS) 1.2 encrypts data as it travels between cloud services and users, ensuring strong authentication, privacy, integrity, and protection against tampering or interception. TLS 1.2 is the default and widely supported.
MACsec (IEEE 802.1AE) adds an additional layer of encryption at the infrastructure level when Azure traffic moves between datacenters, preventing physical attacks like "man-in-the-middle." This hardware-based encryption is automatically enabled, providing seamless protection with no impact on network performance.
Both encryption methods ensure secure and private data transmission with no customer intervention required.
4. DP-4: Enable data at rest encryption by default
Features: Data at Rest Encryption Using Platform Keys
Microsoft Azure encrypts data-at-rest to protect it from ‘out of band’ attacks, such as attempts to access underlying storage. This encryption helps ensure that attackers can't easily read or modify your data. Infrastructure encryption using platform-managed keys. By default, disks are automatically encrypted at rest through platform-managed encryption keys.
No additional configurations are required as this is enabled on a default deployment.










 8. The box for 'Create or customize advanced DLP rules' will be checked by default. Click 'Next' to proceed.
8. The box for 'Create or customize advanced DLP rules' will be checked by default. Click 'Next' to proceed.
.jpg)




































































Comments
Post a Comment