4. Endpoint security
1. ES-1: Use Endpoint Detection and Response (EDR)
1. License:
I have two licenses, Microsoft 365 Business Premium and Microsoft Defender for Endpoint P1, to use for this demo.
2. Download the VDI configuration package file:1. Login to Microsoft Defender Portal (https://security.microsoft.com/)
2. Go to Settings, and then click on Endpoints.
3. Under Device management, click Onboarding6. Under Deployment method, select VDI onboarding scripts for non-persistent devices, then scroll down slightly.
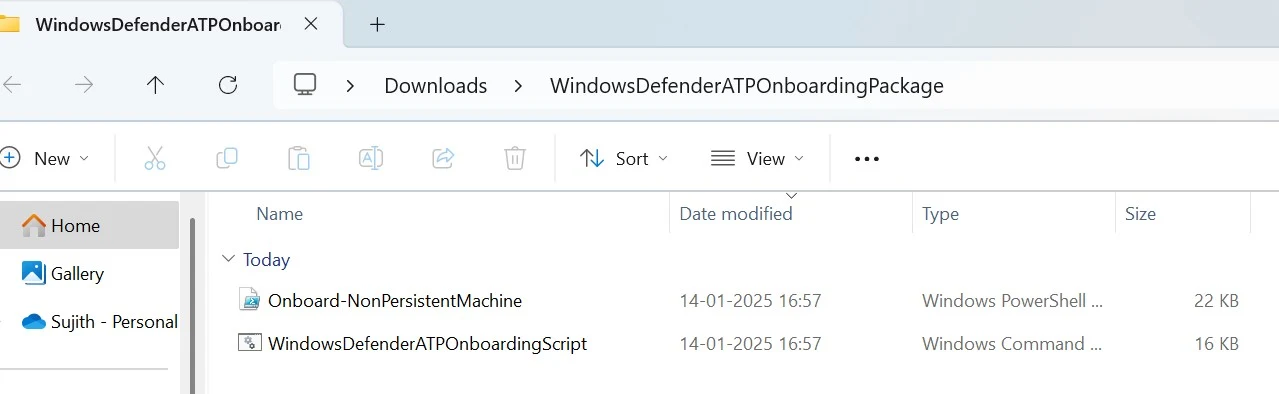
3. Copy Zip File Contents to the Shared Folder:
1. Unzip the File and copy both Onboard-NonPersistentMachine.ps1 and WindowsDefenderATPOnboardingScript.cmd into the shared location
2. I have copied the contents to a shared folder.
4. Use Domain Group Policy:
1.Open the Group Policy Management Console (GPMC). Right-click on the OU intended for AVD Session Hosts and select 'Create a GPO in this domain, and link it here.
2. Give a suitable name and click OK.
3. Right-click the Group Policy Object (GPO) you created and click Edit.
4. Go to Computer configuration > Preferences > Control panel settings.
5. Right-click Scheduled tasks, click New, and then click Immediate Task (At least Windows 7).
6. In the Task window that opens, go to the General tab. Give a Suitable name.
7. Under Security options click Change User or Group and type SYSTEM. Click Check Names and then click OK. NT AUTHORITY\SYSTEM appears as the user account the task will run as.
8. Select Run whether user is logged on or not and check the Run with highest privileges check box.
9. Go to the Actions tab and click New.
10. Action = "Start a program"
11. Program/Script = C:\WINDOWS\system32\WindowsPowerShell\v1.0\powershell.exe
12. Add Arguments (optional) = -ExecutionPolicy Bypass -command "& \\ADVM01\MDE-Onboarding\Onboard-NonPersistentMachine.ps1"
13. Then select OK and Apply. Close the Group Policy Management window.
5. Test:
2. It is successfully onboarded to the Defender Portal.
6. FSLogix Exclusions:1. Antivirus products are known to conflict with FSLogix containers and requires that specific files and folders are excluded from any type of scanning or heuristics.
2. Following File/Folder need to be excluded from scanning:
%TEMP%\*\*.VHD
%TEMP%\*\*.VHDX
%Windir%\TEMP\*\*.VHD
%Windir%\TEMP\*\*.VHDX
\\server-name\share-name\*\*.VHD
\\server-name\share-name\*\*.VHD.lock
\\server-name\share-name\*\*.VHD.meta
\\server-name\share-name\*\*.VHD.metadata
\\server-name\share-name\*\*.VHDX
\\server-name\share-name\*\*.VHDX.lock
\\server-name\share-name\*\*.VHDX.meta
\\server-name\share-name\*\*.VHDX.metadata
Replace the server name and share name as follows:
%TEMP%\*\*.VHD
%TEMP%\*\*.VHDX
%Windir%\TEMP\*\*.VHD
%Windir%\TEMP\*\*.VHDX
\\mdestr01.file.core.windows.net\mdeshare01\*\*.VHD
\\mdestr01.file.core.windows.net\mdeshare01\*\*.VHD.lock
\\mdestr01.file.core.windows.net\mdeshare01\*\*.VHD.meta
\\mdestr01.file.core.windows.net\mdeshare01\*\*.VHD.metadata
\\mdestr01.file.core.windows.net\mdeshare01\*\*.VHDX
\\mdestr01.file.core.windows.net\mdeshare01\*\*.VHDX.lock
\\mdestr01.file.core.windows.net\mdeshare01\*\*.VHDX.meta
\\mdestr01.file.core.windows.net\mdeshare01\*\*.VHDX.metadata
3. Open the Group Policy Management Console (GPMC). Right-click on the OU intended for AVD Session Hosts and select 'Create a GPO in this domain, and link it here. Right-click the Group Policy Object (GPO) you created and click Edit.
4. Go to Computer Condiguration-Policies-Administrative Templates-Windows Components-Windows Defender Antivirus-Path Exclusions
5. Select Enabled and click on Show.
6. Add the files/folders as specified in the value name and set the value to 0.
7. Click OK and Apply.
2. ES-2: Use modern anti-malware software
1. As per the customer’s requirements, you may enable the different Defender plans. However, the Foundational CSPM plan is free and includes the Microsoft Cloud Security Benchmark, which contains over 200 policies that can be applied at no cost to enhance the security posture of our AVD environment.
3. ES-3: Ensure anti-malware software and signatures are updated
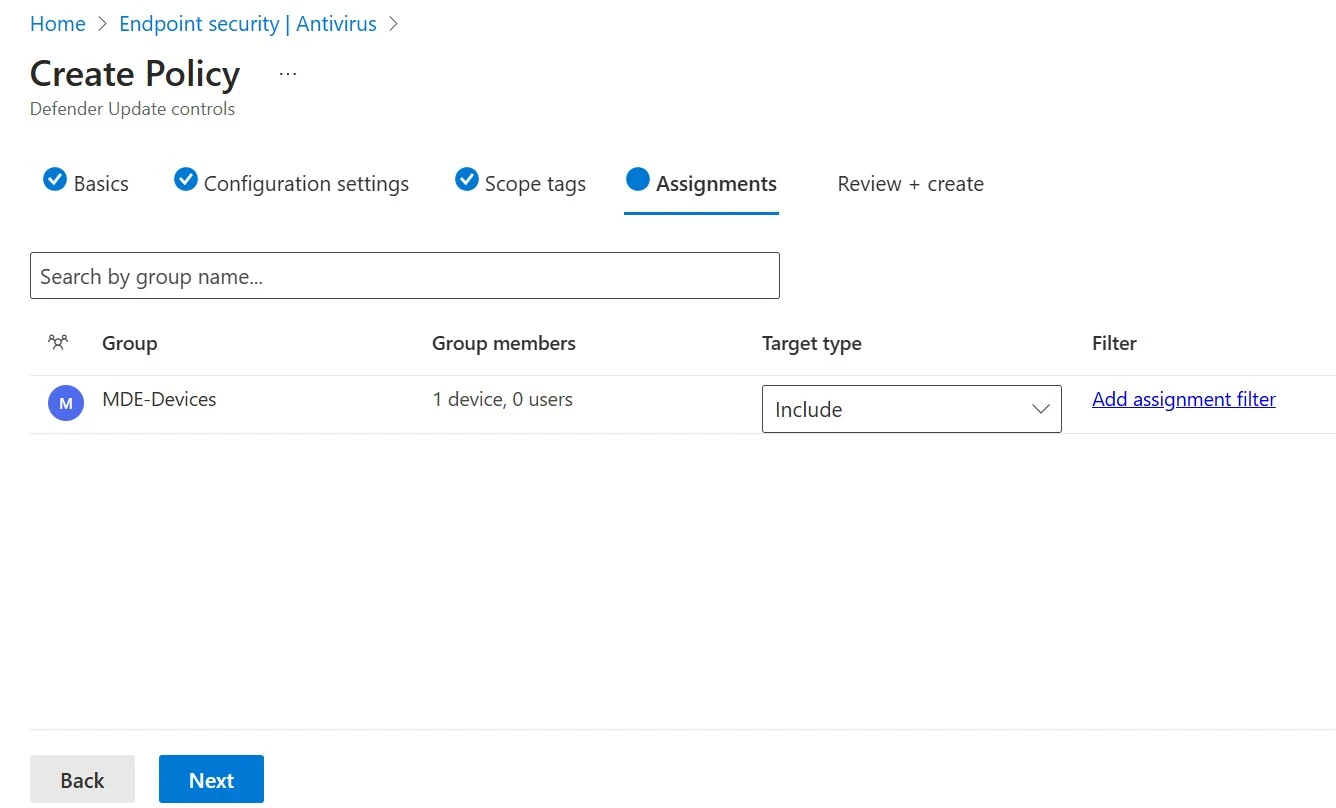
2. I also have a dynamic device security group created to ensure that the AVD session hosts are automatically enrolled into this group upon creation.
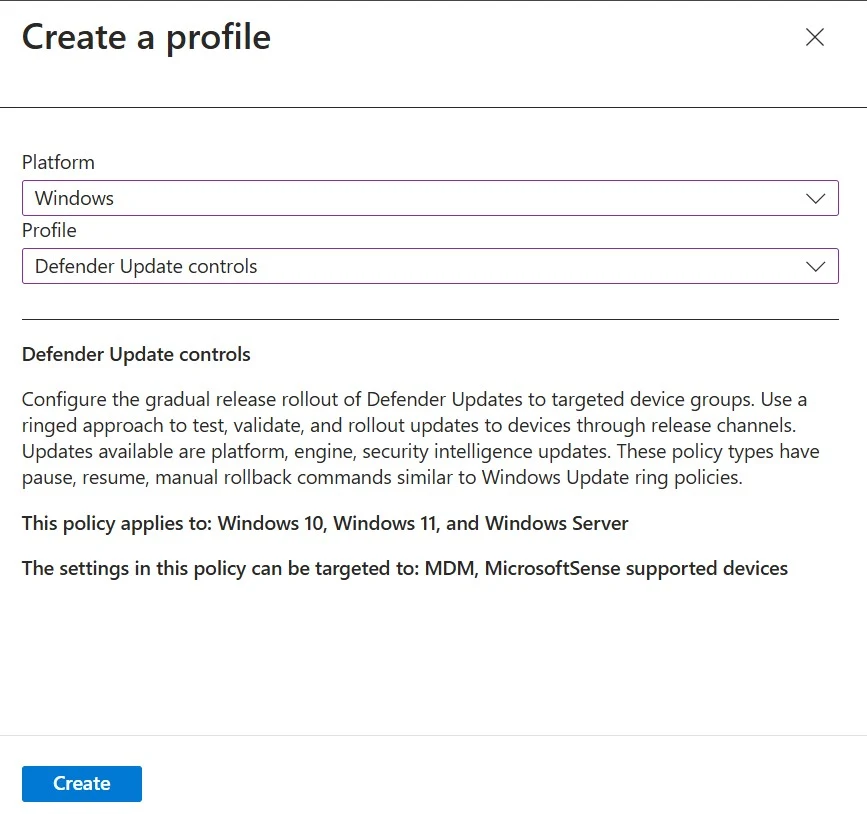
2. Create AV Policy:
8. In the Configuration Settings tab, under Engine Updates Channel, Platform Updates Channel, and Security Intelligence Updates Channel, there are six options, as shown below. You can select any one depending on the customer's requirements.
9. For this demo, I have selected the Preview Channel for the Engine Updates Channel and Platform Updates Channel, while for the Security Intelligence Updates Channel, I have selected the default channel.
15. You should be able to see the engine, platform, security intelligence updates version in the Windows Security tab.


































Comments
Post a Comment