1. What is Azure Landing Zone?
An Azure Landing Zone is like a pre-built foundation for setting up cloud environments in a secure, organized, and scalable way. It includes best practices, security controls, networking, and governance policies, so businesses can quickly deploy their workloads without worrying about misconfigurations. Think of it as a well-planned city layout where roads, utilities, and security are already in place before people move in.
2. Prerequisites:
1. Your ID needs to have Global Administrator permissions.
2. To enable template deployments at the tenant scope, elevate access to manage all Azure subscriptions and management groups. Browse to Microsoft Entra ID > Manage > Properties. Under Access management for Azure resources, set the toggle to Yes and click Save.
3. Run the below commands in Cloud Shell to assign Owner permissions to the user ID being used for the deployment:New-AzRoleAssignment -SignInName "[userId]" -Scope "/" -RoleDefinitionName "Owner"
az role assignment create --assignee "[userId]" --scope "/" --role "Owner"
3. Deployment settings:
1. Navigate to the link: What is an Azure landing zone? - Cloud Adoption Framework | Microsoft Learn and click on 'Deploy to Azure'.
2. For Azure cloud environment, select 'Azure Cloud'. Scroll down slightly.
3. Validate the Directory and the Region, then click Next.
4. Azure Core setup:
1. Under Azure core setup tab, provide a Resource prefix (max 10 characters, unique at tenant-scope). This will be used for the Management Group hierarchy and other resources created as part of this deployment. Scroll down slightly.
2. For 'Platform subscription options', it is recommended to go with the Dedicated option. If 'Dedicated (recommended)' is selected, dedicated Subscriptions will be created for deploying connectivity, identity and management resources. Select Single for testing purposes where all roles will be deployed in a single subscription. A single subscription can be used for proof of concepts, or by smaller organizations.
3. For 'Platform subscription' select the required subscription.
4. For 'Deploy in a secondary region', if you select Yes, you will be prompted to deploy resources in an additional region where appropriate. Here, we have selected 'No'. Scroll down slightly.
5. For Prevent the deployment of classic resources, select Yes.6. For Prevent the deployment of virtual machines and virtual machine scale sets with unmanaged disks, select Yes.
7. For Enforce subnets should be private, select Audit only. Scroll down slightly.
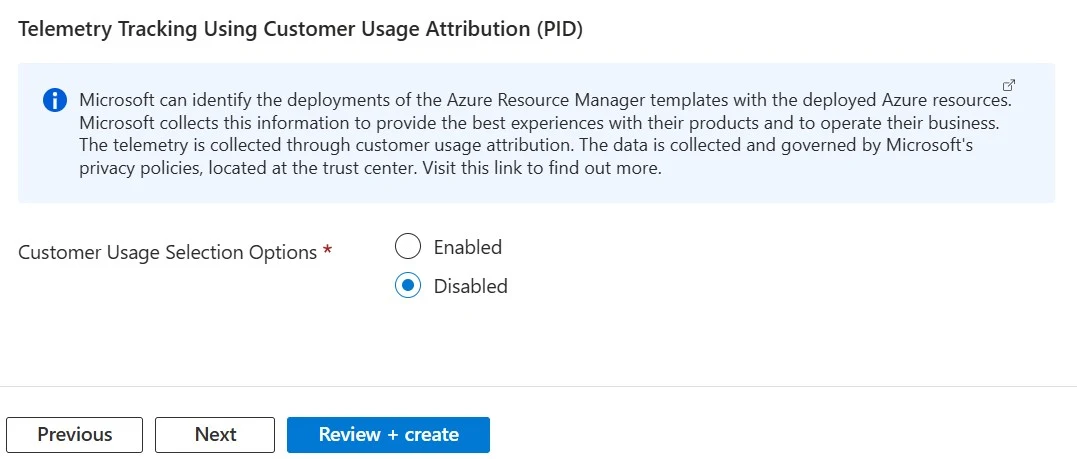
8. For telemetry tracking, you can select either Enabled or Disabled, depending on the customer. 9. Click Next.
5. Platform management, security, and governance :
1. For Enforce Key Vault recommended guardrails, if Yes is selected, an Azure Policy Initiative will be assigned to ensure that the recommended Key Vault policies are enabled. From an AVD perspective, Key Vault is usually not used during deployment unless the Session Host Configuration feature is used, which is currently in Preview. Hence, I have selected No. Scroll down slightly.
Please find the list of policies that will be enabled if you select Yes: Enforce recommended guardrails for Azure Key Vault - Enforce-Guardrails-KeyVault
2. For Enforce Backup and Recovery recommended guardrails, if 'Yes' is selected, Azure Policy Initiative will be assigned to ensure recommended Azure Recovery Services policies are enabled. Scroll down slightly.
Please find the list of policies that will be enabled if you select Yes Enforce enhanced recovery and backup policies - Enforce-Backup
3. For Deploy Log Analytics workspace and enable monitoring for your platform and resources, select 'No'. Click Next.
The reason is: If you select Yes, you will also get the following options to enable or disable::
Select Diagnostic Settings logging category-Not all diagnostic settings need to be configured from an AVD perspective. Only the logs required and recommended for AVD deployment should be selected. (Refer to Setting Up AVD Insights for Effective Monitoring of Your Azure Virtual Desktop Environment - A T L)
Deploy Microsoft Sentinel (configuration required to activate) -This involves additional costs. Customers should review the plan and pricing before enabling Sentinel.
Deploy Change Tracking-Not required based on the recommended logs for AVD deployment.
Deploy Azure Update Manager-Windows 10 and Windows 11 OS are not supported.
Deploy VM Insights-When insights are enabled for AVD, all session hosts will be covered.
Deploy Microsoft Defender for Cloud and enable security monitoring for your platform and resources -The Foundational CSPM plan is free and includes the Microsoft Cloud Security Benchmark, which offers over 200 policies to enhance the security posture of the AVD environment. However, most of these policies are not required for AVD. It is recommended to review each policy individually before assigning them. Based on my experience, around 26 essential policies are required for AVD. Feel free to add more if necessary. Refer to Azure Security Baselines for Azure Virtual Desktop-Asset Management - A T L
6. Baseline alerts and monitoring:
1. For Deploy Service Health Alerts, select Yes.
Deploying Service Health Alerts is important from an AVD (Azure Virtual Desktop) perspective because it helps you stay informed about any issues or outages affecting Azure services that your AVD environment depends on.
Scroll down slightly.
2. Select Yes for all the options below, then scroll down slightly.
3. Select Yes to enable AMBA for alterations in network routing and security. For the rest, select No. Scroll down slightly.4. Select No to enable AMBA for web services. For the rest, select Yes. Scroll down slightly.
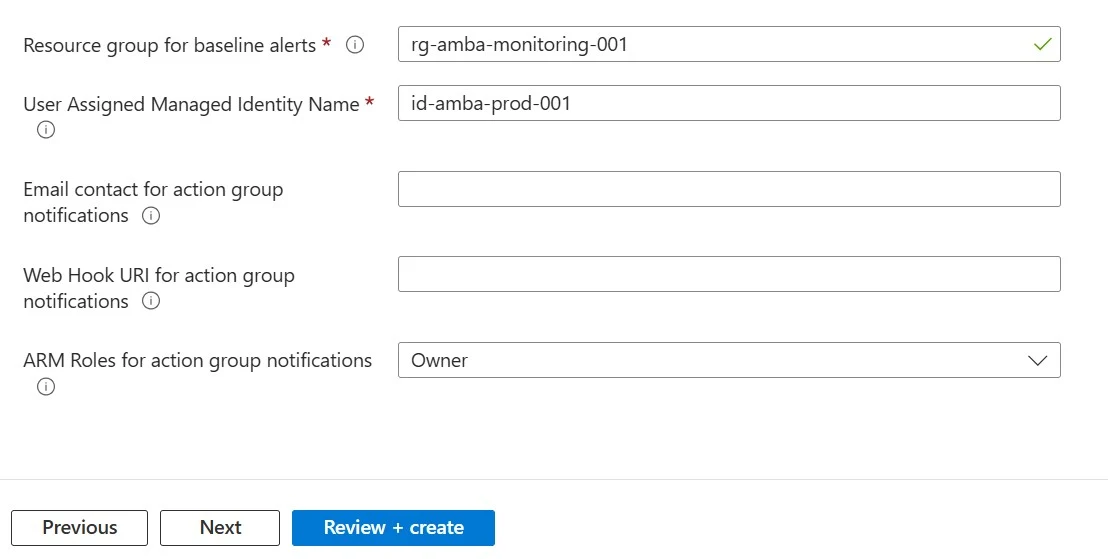
5. The Resource group name and user assigned managed identity is auto-populated. Click Next.7. Network topology and connectivity:
1. The networking components, such as site-to-site VPN and the hub-and-spoke model, should be configured separately from the landing zone. Doing so will prevent increasing the deployment time and reduce the risk of complications in case the deployment fails. If the deployment fails, it can be confusing for admins to determine which resources need to be redeployed. Additionally, creating the connectivity separately allows us to focus more on the specific settings that need to be configured. Click Next.
8. Identity:
1. Under the Identity tab, for Ensure Azure VMs (Windows & Linux) are enabled for Azure Backup, select No. The reason is that for Pooled AVD, data is stored on Azure Files and not on the VMs
2. For the rest, select Yes.
3. Click Next.
9. Landing zones configuration:
1.Select Yes or No for the corresponding options, as shown in the screenshots below. We are selecting Yes only for components relevant to the AVD perspective.
3. Click Next.
10. Workload specific compliance:
1.We are selecting only the workloads relevant to AVD. For all others, we are selecting No.
2. Click Next.
11. Decommissioned/Sandbox:
1. Select No.
12. Regulatory Compliance:
1. Select No.
2. Click Next.
13. Review +Create:
1. Click Create.
2. The deployment is completed.
14. FAQs:
Please refer to the link for frequently asked questions on Landing Zone configuration:



































Comments
Post a Comment